Blog
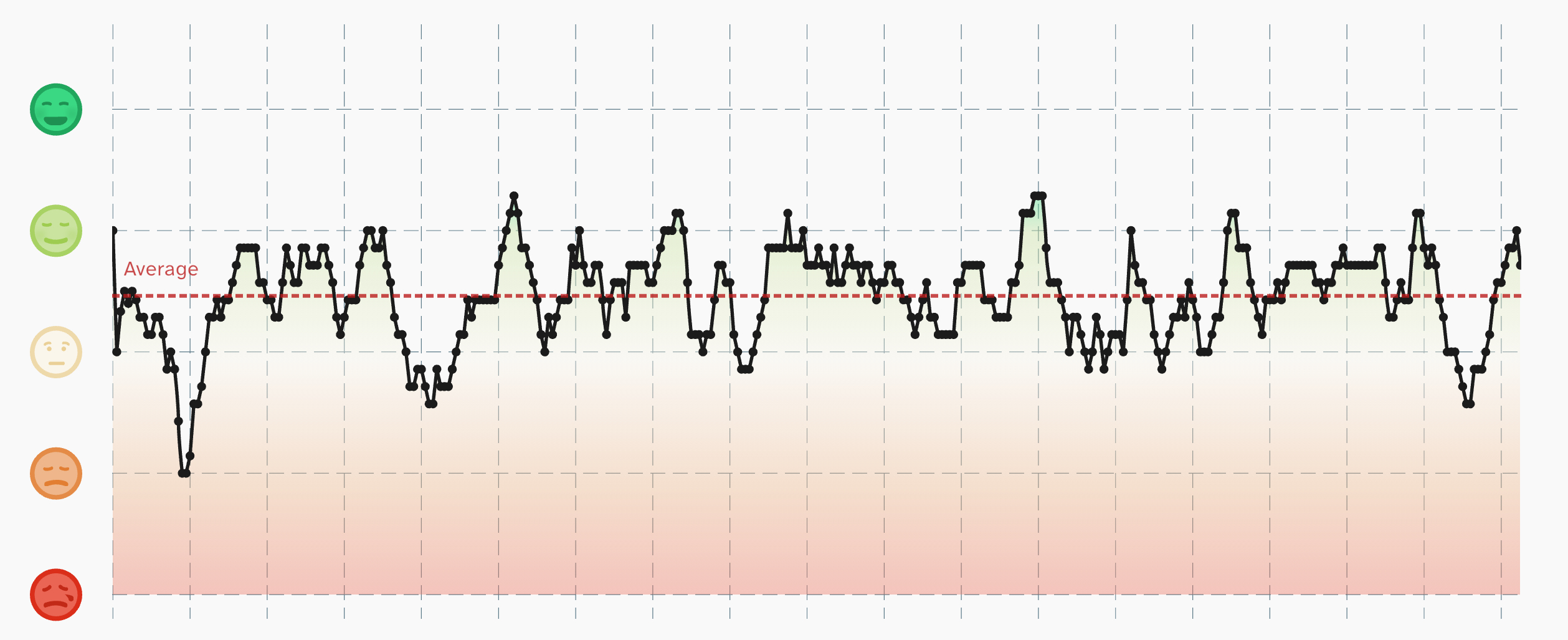
Awareness First: One Year of Mental Health Tracking
Published by Muoi Tran on January 4, 2025
Mental health is a cornerstone of overall well-being. Yet, it is often overlooked, especially in high-pressure environments like academia, where the combination of intellectual rigor, long working hours, and frequently...

Taming the transient while reconfiguring BGP
Published by Tibor Schneider on October 24, 2023
Network operators reconfigure their networks daily to adapt to new business relationships, optimize network performance, or perform regular maintenance. Applying such reconfigurations is nerve-racking as they often...

[Podcast] Is my Internet Down?
Published by Ege Cem Kırcı on February 2, 2023
In this episode of PING, Ege Cem Kirci from the Networked Systems Group at ETH Zurich discusses his IMC paper on user perceptions of Internet outages, measured with Google Trends. This was presented at the IMC...
Building an Internet Router on top of ChatGPT
Published by Laurent Vanbever on December 5, 2022
ChatGPT by OpenAI recently took the Internet (and your timelines) by storm. One of the coolest and most creative use of ChatGPT I encountered thus far was to show that it can behave as a Linux-based Virtual Machine. That...

ACC-Turbo mitigates pulse-wave DDoS attacks using programmable switches
Published by Albert Gran Alcoz on October 26, 2022
Pulse-wave Distributed Denial-of-Service (DDoS) attacks have recently managed to take down critical network infrastructure causing enormous financial and reputational damage. In contrast to conventional DDoS attacks,...
ditto prevents traffic-analysis attacks in WANs
Published by Roland Meier on May 6, 2022
Many existing attacks on the Internet show that network traffic leaks lots of information about ongoing activities even if it is encrypted. These so-called traffic-analysis attacks leverage the fact that encryption does...

Published by Laurent Vanbever on April 13, 2021
Teaching online for >1 year… Who would have thought? In this short, low-key presentation, I reflect on how we evolved our lectures over the last 3 semesters to improve students’ experience. Also on Twitter Teaching...
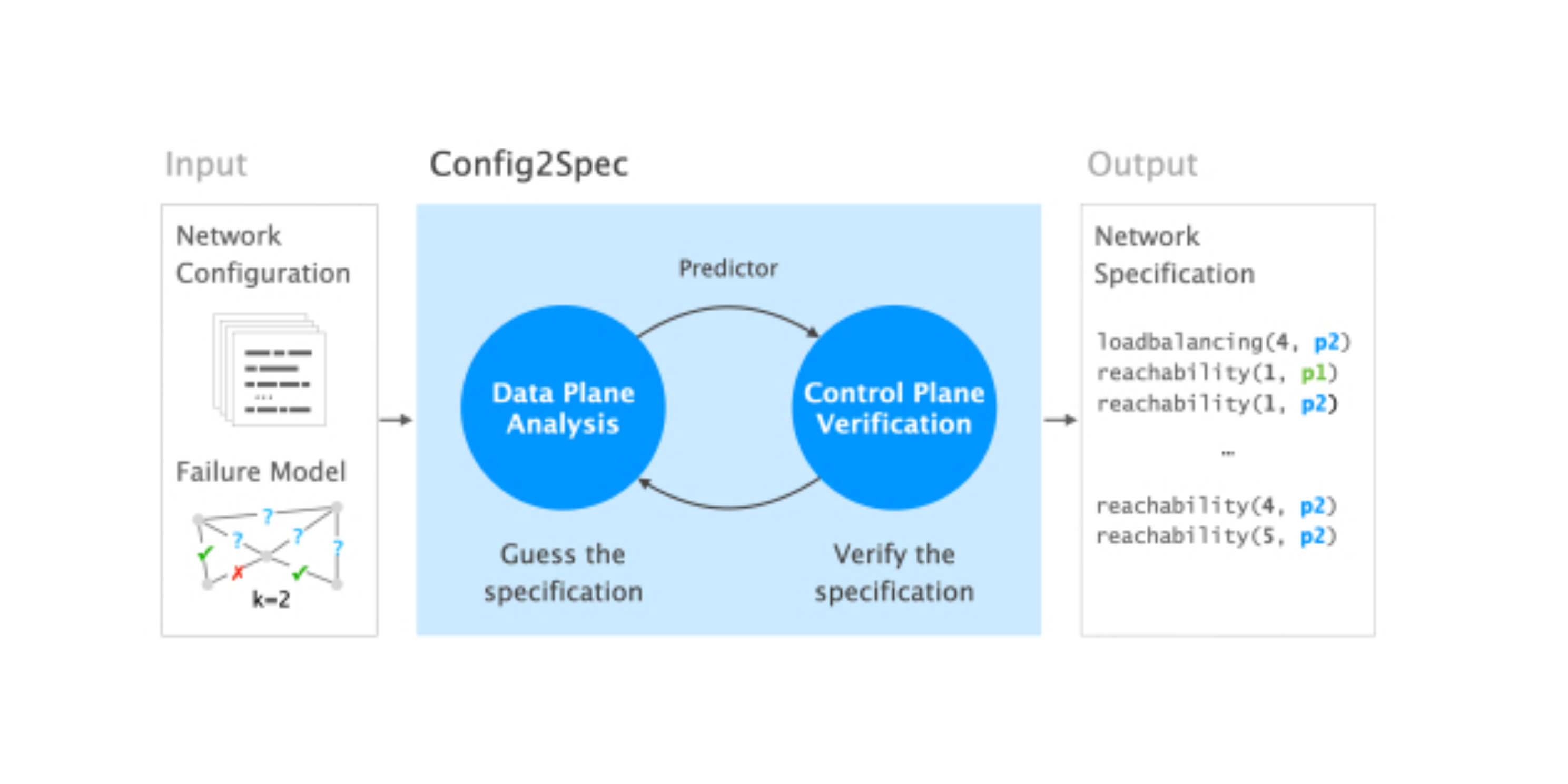
Config2Spec: Mining network specifications from network configurations
Published by Rüdiger Birkner on March 8, 2021
For several years now, the community has been dreaming of Intent-Based Networking (IBN): the idea of telling the network what to do instead of how to do it. An operator should, for example, be able to simply state its...

NetDice verifies your SLAs using probabilistic analysis
Published by Samuel Steffen on October 15, 2020
Arguably, the most effective method to prevent downtime due to network misconfigurations is detecting them before configurations are deployed. Network verification, which is concerned with checking properties such as...
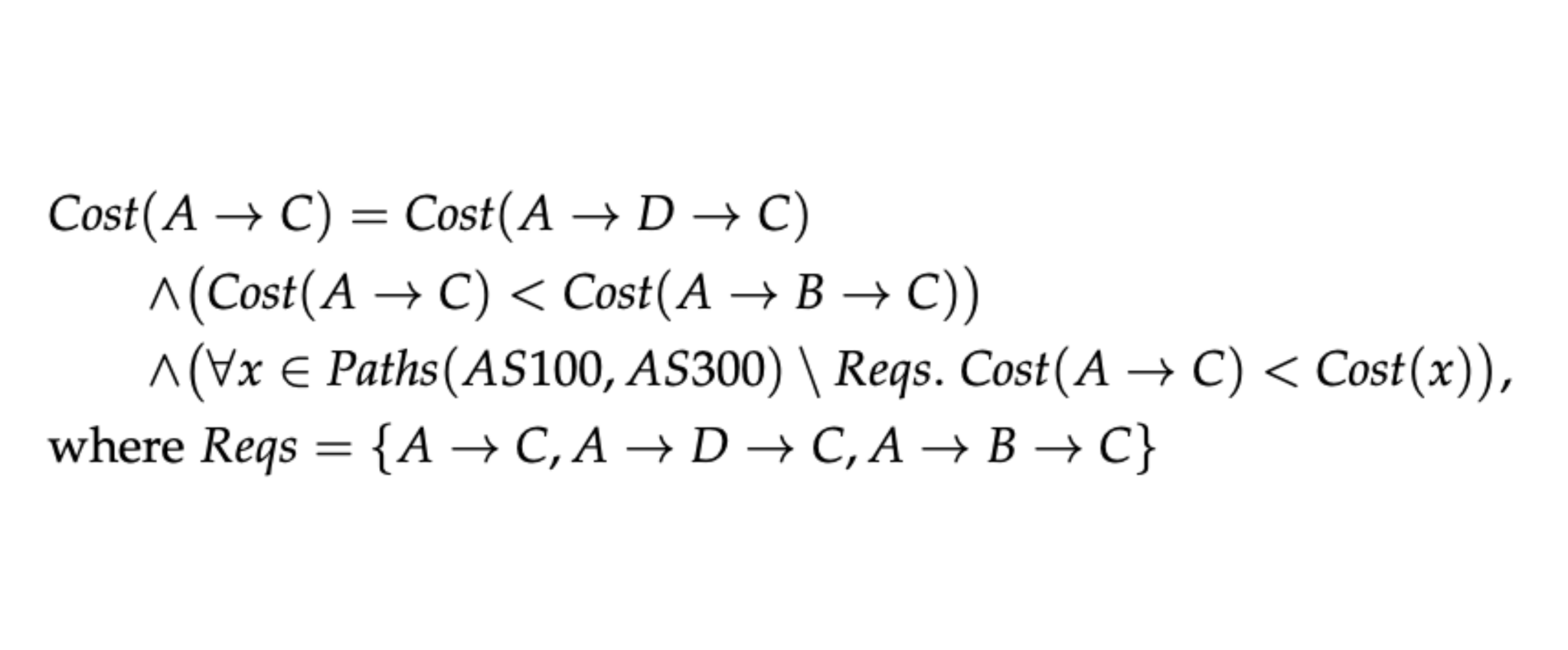
You can’t verify what you can’t specify
Published by Laurent Vanbever on May 11, 2020
Back when I was studying for my master degree, Prof. Axel van Lamsweerde was teaching us formal logic. Axel is world-famous for his works on requirements engineering, that is, the process of defining and maintaining the...

Develop your own mini-Internet to teach students virtually about network operations
Published by Thomas Holterbach on April 14, 2020
The Internet is a large network of networks that is managed by thousands of people around the globe. Despite the rather simple concepts on which it is based, operating the Internet requires complex distributed operations...