ditto prevents traffic-analysis attacks in WANs
Research areas: Network Security, and Network Programmability
Published by Roland Meier on May 6, 2022
Originally written for the APNIC Blog
Many existing attacks on the Internet show that network traffic leaks lots of information about ongoing activities even if it is encrypted. These so-called traffic-analysis attacks leverage the fact that encryption does not (or only slightly) change traffic metadata such as the sizes of packets, the time between packets, and the number of packets. Past works show that it is possible to infer the contents of VoIP calls, streamed movies, visited websites, or the device identities without having to break any encryption.
Most published defence techniques focus on preventing traffic-analysis attacks on Internet traffic and there is little work that examines Wide Area Networks (WANs) even though such networks are susceptible too (as we know from the Snowden revelations, for example).
This blog post explains why there is a need for WAN-specific traffic-analysis prevention systems and it presents a possible solution based on programmable data planes.
Why WANs are at risk
WANs typically consist of dedicated high-bandwidth links (often 100s of Gbps) and provide fast and reliable connections between different sites of an organization (for example, different data centres).
By nature, WAN links span over large geographical distances and are almost impossible to secure against wiretapping. Major operators (for example, Microsoft, Amazon, and OVH) acknowledge this risk and encrypt their WAN traffic not only on the application layer but also on the link layer using MACsec.
However, as the traffic-analysis attacks mentioned above have shown, encryption is not enough. In addition to encryption, traffic metadata (for example, the size, timing, and number of packets) needs to be hidden from an eavesdropper too.
The most common way to prevent traffic-analysis attacks is to obfuscate traffic metadata by adding padding to packets, sending packets at a constant rate, and injecting dummy packets. There already exist several systems that do this for application traffic over the Internet (for example, for web browsing). However, these systems are designed for traffic over shared links and cannot be applied in WANs because they introduce too much overhead and provide too small throughput, and require changes at end hosts.
With ditto, we at ETH Zürich and armasuisse have developed a system that is tailored to WANs. It adds little overhead, provides high throughput, does not require any changes to end hosts, and provides high security.
ditto: a system tailored to WANs
The high-level idea behind ditto is to make traffic observed by an eavesdropper follow a predefined pattern regarding packet sizes and timings in addition to encrypting the packets. This makes the observed traffic independent of the real traffic in the network.
Figure 1 shows an example of this: The output of ditto (right side) are packets alternating between two sizes and they are sent at a fixed rate. Since the traffic metadata are then independent of the real traffic and all packets are encrypted, traffic analysis is no longer possible.
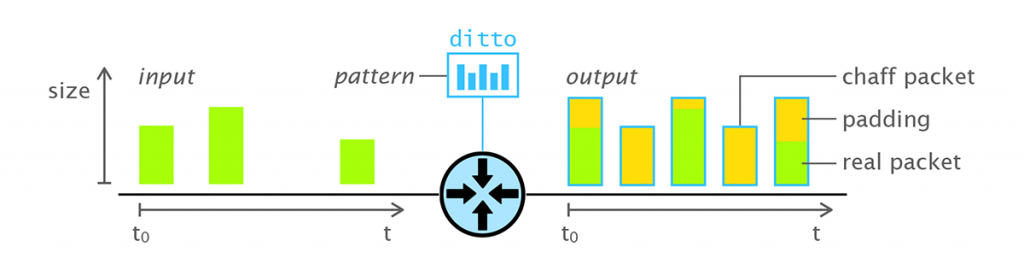
Figure 1 — ditto shapes real traffic (the green boxes on the left) into a predefined pattern (right) regarding packet sizes and timings.
To shape traffic into a predefined pattern, ditto uses three operations:
- Padding of incoming packets, to regularize their sizes.
- Buffering/delaying of incoming packets, to regularize their timings and their relative order.
- Insertion of chaff packets, to fill any possible gaps and ensure the consistency of the packet rates.
In contrast to existing work, ditto performs these actions in the network data plane (not on end-hosts or servers) and it operates on a per-link basis (not per-flow). This significantly reduces the overhead because ditto only adds padding or chaff packets when there is no real traffic to send.
The key enabler for ditto is recent advances in network programmability that make it possible to implement custom applications on network switches that run them at line rate — potentially processing terabits of traffic per second in one switch. While P4, the programming language for these applications, is limited (for example, there are no loops, no floating-point operations, and the hardware usually has very little memory), we show that shaping traffic into a predefined pattern is possible by using components that are part of (programmable) network switches: priority queues, round-robin scheduling, and custom packet headers.
We fully implemented a prototype of ditto (the code is open source) and we evaluated it with real Internet backbone traffic. Our results show that ditto runs at a 100Gbps line rate and performs with negligible performance overhead up to a realistic traffic load of 70Gbps per WAN link. Above this traffic load, ditto starts to have an impact on network performance, but it still ensures that traffic-analysis attacks are not possible.
More information and resources
Our paper, published at NDSS 2022, provides more information about ditto and the source code is available on GitHub.
ditto is one of the results of a joint research project between ETH Zürich and armasuisse. The goal of the research project is to investigate how network programmability can be used to increase the security of computer networks and the anonymity and privacy of their users.

